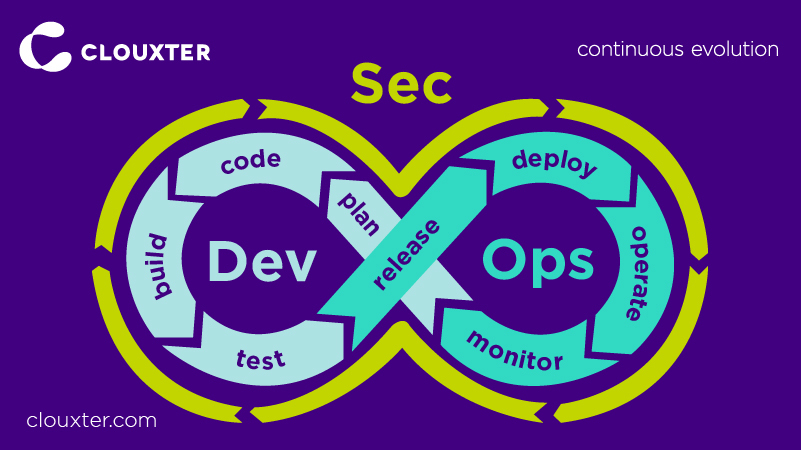
The use of this cyclical tool is key for organizations to provide guarantees in software production under the DevOps culture. This means reducing risks and vulnerabilities to a minimum.
DevSecOps, the champion of security in times of cybercriminals
Massification in the use of information and communications technologies (IT) – global coverage of 105 percent of cellular mobile subscriptions and 51.4 percent of Internet use according to the International Telecommunications Union (ITU) – is the favorable scenario for cybercrime.
Massification in the use of information and communications technologies (IT) – global coverage of 105 percent of cellular mobile subscriptions and 51.4 percent of Internet use according to the International Telecommunications Union (ITU) – is the favorable scenario for cybercrime. According to Statista, the one that caused the most damage occurred in 2018 and harmed 1.1 billion users of Aadhaar, India’s Digital Identification system.
Despite these facts, there is also progress in creating environments to contain cybercrime. The most recent report from Interpol and BT Group, a global provider of telecommunications services, revealed that “76% of business leaders rate their organization as excellent or good at protecting themselves from cybersecurity threats.”
How to implement DevSecOps in an organization?
According to Suárez, there are three steps to follow. The first is to introduce security standards throughout the software development lifecycle, the second is for all teams to share the responsibility of following security best practices, and the third is to enable automatic security checks at all stages of development. software delivery.
If you want more details about this methodology, we invite you to our YouTube channel where Ricardo González, Chief Technology Officer of Clouxter, explains in-depth
Ricardo González, CTO of Clouxter
The DevSecOps Usage Cycle covers other phases
- The first is planning, in which work teams must carry out an analysis to establish where, how, and when security tests will be carried out.
- The second is the coding in which the components are evaluated to detect vulnerabilities. The third phase is the construction of the applications in which the number of analyses increases.
- The fourth is the test consisting of the continuous monitoring of the processes and subjecting the application to exams in which its response to highly complex problems is measured.
The remaining phases in this process of executing DevSecOps tools are related to launch, deployment, implementation, and monitoring. In other words, this covers protecting the runtime infrastructure, deploying the build artifact to production, and monitoring applications by introducing more security measures.
Fundamentally, as software production continues to scale, IT teams must ensure that this process unfolds under the highest security standards. The tool that offers this is DevSecOps, a model that should be consistently replicated and applied in an automated environment, to shield organizations from cybercrime.